Threat Intelligence Blog

Contact us to discuss any insights from our Blog, and how we can support you in a tailored threat intelligence report.
Article in the current edition of the Guernsey Chamber of Commerce Contact magazine - 'Uncomfortable Truths: How any Director or NED poses a major Information Security Risk'
Article in the current edition of the Guernsey Chamber of Commerce Contact magazine - 'Uncomfortable Truths: How any Director or NED poses a major Information Security Risk'
Do you need to worry about the security of internet connected things? Hint - if we're doing a video about then then answer is probably yes! Cyber Tip Tuesday video
Do you need to worry about the security of internet connected things? Hint - if we're doing a video about then then answer is probably yes! Cyber Tip Tuesday video
Cyber Weekly Flash Briefing 25 September 2020: GFSC consult on new Cyber Rules; FinCEN leak exposes poor data security; Zerologon attacks detected; ransomware gang behind German hospital death
Cyber Weekly Flash Briefing 25 September 2020: GFSC consulting on new Cyber Rules; Leaked FinCEN files expose poor data security; Microsoft detects active Zerologon attacks; ransomware crew fingered for German hospital death; malware that steals your most sensitive data on the rise; Ransomware is evolving; top threats inside malicious emails; Credential Stuffing behind Recent Attacks
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
GFSC new Cyber Rules and Guidance out for consultation
The GFSC have put the Cyber Security Rules and Guidance Consultation Paper up on their website and consultation hub.
Why this matters:
The new rules and accompanying guidance came out of the 18 month thematic review which ended last year, which found that regulated financial service firms within the Bailiwick of Guernsey were not taking risks from cyber threats seriously enough and were lacking in appropriate protections and controls. These new rules seek to rectify this but many firms on the Island are going to have to do work to become compliant, especially around their ability to monitor for and detect unusual activity that could be indicative of a actual or attempted intrusion or breach.
The rules and guidance can be found here:
Leaked FinCEN files expose poor data security
Leaked documents, dubbed the “FinCEN Files,” describe global money laundering of $2 trillion processed by many of the world’s biggest banks between 2000 and 2017. The reveal illuminates the struggle for the financial industry and government to provide ironclad data protection.
“This sensational and unprecedented leak clearly demonstrates a wide spectrum of data protection weaknesses in the governmental sector, affecting even the most developed Western countries,” Ilia Kolochenko, founder and CEO of ImmuniWeb, said of the files.
“From a cybersecurity standpoint, we may expect a growing lack of trust to governmental agencies, which on one side have quasi-unlimited access to the most sensitive data of the largest organisations, while cannot duly safeguard this data on the other side,” he said.
The latest disclosure exposing apparently insufficient attempts by the public and private sectors to curb corruption came to light in a BuzzFeed News report which detailed more than 2,500 reported cases, including 2,100 Suspicious Activity Reports (SAR) filed by financial institutions with the U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN).
JPMorgan Chase, Citigroup, Bank of America, Deutsche Bank, HSBC and Standard Chartered are among the financial institutions cited in the leaked files as processing dirty money around the world. The documents may have come from a whistleblower or insider at FinCEN. The International Consortium of Investigative Journalists (ICIJ), which represents 108 news organizations in 88 countries, is conducting a probe of the matter.
Why this matters:
Other similar investigative reports on similar wrongdoing focused single financial, tax or legal institutions, such as the 2017 Panama Papers emanating from clients of the law firm Mossack Fonseca. But the FinCEN docs reveal that a wide array of people from oligarchs and corrupt politicians to drug dealers and organised crime throughout the world know how to circumvent the system’s supposed checks and balances.
Read more: https://www.scmagazine.com/home/security-news/leaked-fincen-files-expose-poor-data-security/
Microsoft says it detected active attacks leveraging Zerologon vulnerability
Hackers are actively exploiting the Zerologon vulnerability in real-world attacks, Microsoft's security intelligence team said this week.
The attacks were expected to happen, according to security industry experts.
Multiple versions of weaponized proof-of-concept exploit code have been published online in freely downloadable form since details about the Zerologon vulnerability were revealed a week ago.
The first proof-of-concept exploit was published hours after the explanatory blog post, confirming initial analysis that the Zerologon bug is easy to exploit, even by low-skilled threat actors.
Why this matters:
Put simply the Zerologon bug is a vulnerability in Netlogon, the protocol used by Windows systems to authenticate against a Windows Server running as a domain controller. Exploiting the Zerologon bug can allow hackers to take over the domain controller, and inherently a company's internal network.
Zerologon was described by many as the most dangerous bug revealed this year. US federal agencies were given three days to patch domain controllers or disconnect them from federal networks.
As several security experts have recommended since Microsoft revealed the attacks, companies that have their domain controller exposed on the internet should take systems offline to patch them.
These internet-reachable servers are particularly vulnerable as attacks can be mounted directly, without the hacker first needing a foothold on internal systems.
Doppelpaymer ransomware crew fingered for attack on German hospital that caused death of a patient
The Doppelpaymer ransomware gang were behind the cyber-attack on a German hospital that led to one patient's death, according to local sources.
A German newspaper carried a report that Doppelpaymer's eponymous ransomware had been introduced to the University Hospital Düsseldorf's network through a vulnerable Citrix product.
That ransomware infection, activated last week, is said by local prosecutors to have led to the death of one patient who the hospital was unable to treat on arrival. She died in an ambulance while being transported to another medical facility with functioning systems.
Why this matters:
According to a report handed to the provincial government of North Rhine-Westphalia and seen by the German Press Association (DPA), the ransomware's loader had been lurking on the hospital's network since December 2019, the same month a patch was issued by Citrix for CVE-2019-19781 – the same vuln exploited to hit the hospital.
Whilst this is the first time a loss of life has been directly attributed to ransomware the threats are increasing all the time.
Vulnerabilities must be patched as soon as possible to stop known vulnerabilities from being used in attacks.
Read more: https://www.theregister.com/2020/09/23/doppelpaymer_german_hospital_ransomware/
“LokiBot,” the malware that steals your most sensitive data, is on the rise
Agencies in the US have reported seeing a big uptick in infections coming from LokiBot, an open source DIY malware package for Windows that’s openly sold or traded for free in underground forums. It steals passwords and cryptocurrency wallets, and it can also download and install new malware.
The increase was measured by an automated intrusion-detection system for collecting, correlating, analysing, and sharing computer security information.
US cyber agency CISA observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020 according to an alert issued this week.
Why this matters:
While not quite as prevalent or noxious as the Emotet malware, LokiBot remains a serious and widespread menace. The infostealer spreads through a variety of methods, including malicious email attachments, exploitation of software vulnerabilities, and trojans sneaked into pirated or free apps. Its simple interface and reliable codebase make it attractive to a wide range of crooks, including those who are new to cybercrime and have few technical skills.
Ransomware is evolving, but the key to preventing attacks remains the same
Ransomware attacks are getting more aggressive according to a senior figure at Europe's law enforcement agency, but there are simple steps which organisations can follow to protect themselves – and their employees – from falling victim to attacks.
"Ransomware is one of the main threats," said the head of operations at Europol's European Cybercrime Centre (EC3). Europol supports the 27 EU member states in their fight against terrorism, cybercrime and other serious and organised forms of crime.
"Criminals behind ransomware attacks are adapting their attack vectors, they're more aggressive than in the past – they're not only encrypting the files, they're also exfiltrating data and making it available," he explained. "From a law enforcement perspective, we have been monitoring this evolution."
Why this matters:
This year has seen a rise in ransomware attacks where cyber criminals aren't just encrypting the networks of victims and demanding six-figure bitcoin payment to return the files, but they're also threatening to publish sensitive corporate information and other stolen data if the victim doesn't pay the ransom.
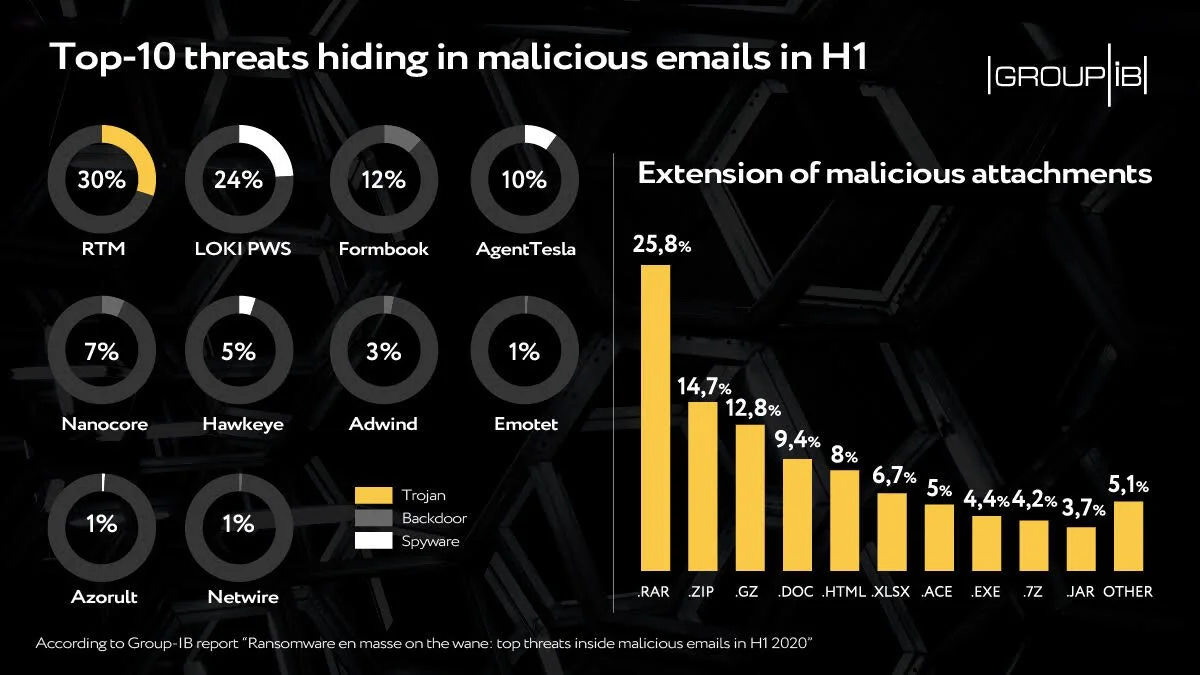
A look at the top threats inside malicious emails
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages, Group-IB reveals.
Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analysed contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware, and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
According to the data, in H1 2020 detected malicious emails were:
43 percent of the malicious mails had attachments with spyware or links leading to their downloading
17 percent contained downloaders
16 percent had backdoors
15 percent had banking trojans
Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
Why this matters:
These findings confirm adversaries’ growing interest in Big Game Hunting. Ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Read more: https://www.helpnetsecurity.com/2020/09/21/top-threats-inside-malicious-emails/
Credential Stuffing: the Culprit of Recent Attacks
A year ago, researchers found that 2.2 billion leaked records, known as Collection 1-5, were being passed around by hackers. This ‘mega leak’ included 1.2 billion unique email addresses and password combinations, 773 million unique email addresses and 21 million plaintext passwords. With this treasure trove, hackers can simply test email and password combinations on different sites, hoping that a user has reused one. This popular technique is known as credential stuffing and is the culprit of many recent data breaches.
There are only a few months left of 2020 but this year has seen its fair share of major data breaches including:
Marriott International experienced another mega breach, when it was still recovering from the 2018 data breach that exposed approximately 339 million customer records
Zoom became a new favourite for hackers due to the remote working mandated in many parts of the world - in early April Zoom fell victim to a credential stuffing attack, which resulted in 500,000 of Zoom’s usernames and passwords being exposed on the Dark Web.
GoDaddy, the world’s largest domain registrar confirmed in April that credentials of 28,000 of its customer web hosting accounts were compromised in a security incident back in October 2019.
Nintendo - in March, users reported unauthorised logins to their accounts and charges for digital items without their permission. In June Nintendo advised that approximately 300,000 accounts were affected by the breach, resulting in the compromise of personal identifiable information such as email address, date of birth, country and gender.
Why this matters:
It has become evident that many of the recent data breaches were the result of credential stuffing attacks leveraging compromised passwords or passphrases. Credential stuffing attacks are automated hacks where stolen usernames and password combinations are thrown at the login process of various websites in an effort to break in. With billions of compromised credentials already circulating the Dark Web, credential stuffing attacks can be carried out with relative ease and with a 1-3% success rate.
When the account of an employee is compromised, hackers can gain access to sensitive data that organisation has collected, and sell it on the Dark Web. The stolen data, often including login credentials, can then be used to infiltrate other organisations’ systems which creates a never-ending cycle.
This is why the LinkedIn breach was blamed for several secondary compromises due to users recycling their exposed LinkedIn passwords on other sites.
Read more: https://www.infosecurity-magazine.com/blogs/credential-stuffing-recent-attacks/
What is the CIA Triad? You're probably heard it mentioned but what is it, and why do you need to know it - Cyber Tip Tuesday video
What is the CIA Triad?
In any conversation you may have been involved in relating to cyber or information security you may have heard reference to the 'CIA triad' - but what exactly is it? And why you need to know what it represents
What is the CIA Triad?
In any conversation you may have been involved in relating to cyber or information security you may have heard reference to the 'CIA triad' - but what exactly is it?
And why you need to know what it represents
Cyber Weekly Flash Briefing 18 Sept 2020: Higher cyber losses; old MS Office exploit; banking Trojan given away free; new Bluetooth flaw; IoT risks; DDoS attacks up; US charge Iranians & Russians
Cyber Weekly Flash Briefing 18 September 2020: Cyber losses increasing in frequency & severity, decade-old MS Office exploit, Cerberus banking Trojan released for free to attackers, Bluetooth vulnerability affects billions of devices, The Internet of Things devices that could put you at risk from hackers
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Cyber losses are increasing in frequency and severity
Research by a cyber insurance provider in North America shows cyber attacks have increased in number and severity since the onset of the coronavirus pandemic. The changes that organisations implemented to facilitate remote work have given cyber criminals new opportunities to launch campaigns exploiting mass uncertainty and fear.
The severity of ransomware attacks has increased since the beginning of COVID-19, with researchers having observed a 47% increase on top of a 100% increase in Q1 2020.
Researchers also found that newer strains of ransomware have been particularly malicious, with costly ransom demands and criminal actors threatening to expose an organisation’s data if they don’t pay. They report that the average demand from attackers using the Maze variety of ransomware is approximately six times larger than the overall average.
Researchers also reported a 35% increase in funds transfer fraud and social engineering claims filed by their policyholders since the pandemic began. Reported losses from these types of attack have ranged from the low thousands to well above $1 million per event.
Additionally, COVID-19 has resulted in a notable surge of business email compromise. The insurer observed a 67% increase in the number of email attacks during the pandemic.
Why this matters:
The report refers to North America but the findings are applicable to us all. They indicate that the most frequent types of losses incurred by victims were from ransomware (41%), funds transfer loss (27%), and business email compromise incidents (19%) — accounting for 87% of reported incidents and 84% of the insurer’s claim pay-outs in the first half of 2020.
Clearly with the landscape getting worse, firms more likely to fall victim, and with losses increasing all the time, firms should ensure they are taking these threats seriously.
Read more: https://www.helpnetsecurity.com/2020/09/14/cyber-losses-are-increasing-in-frequency-and-severity/
Hackers have revived a decade-old Microsoft Office exploit - and they’re having a field day
Hackers have ramped up attempts to abuse a decade-old Microsoft Office flaw with the help of creative new email scams, new research has found.
According to analysis commissioned by NordVPN, attempts to exploit the vulnerability (CVE-2017-11882) rose by 400% in the second quarter of the year - with further growth expected.
Why this matters:
If exploited successfully, the memory corruption bug could allow attackers to execute code on the target device remotely. This is especially problematic if the affected user’s account has administrative privileges, in which case the hacker could seize control of the system.
Cerberus banking Trojan source code released for free to cyber attackers
The source code of the Cerberus banking Trojan has been released as free malware on underground hacking forums following a failed auction.
The leaked code, distributed under the name Cerberus v2, presents an increased threat for smartphone users and the banking sector at large.
Why this matters:
Cerberus is a mobile banking Trojan designed for the Google Android operating system. In circulation since at least July 2019, the Remote Access Trojan (RAT) is able to conduct covert surveillance, intercept communication, tamper with device functionality, and steal data including banking credentials by creating overlays on existing banking, retail, and social networking apps.
The malware is able to read text messages that may contain one-time passcodes (OTP) and two-factor authentication (2FA) codes, thereby bypassing typical 2FA account protections. OTPs generated through Google Authenticator may also be stolen.
Critical Bluetooth security vulnerability could affect billions of devices worldwide
A new security flaw in the Bluetooth software stack discovered over the summer has the potential to affect billions of smartphones, laptops and IoT devices using the Bluetooth Low Energy (BLE) protocol.
The new vulnerability has been given the name BLESA (Bluetooth Low Energy Spoofing Attack) by the team of seven academic researchers at Purdue University who first discovered it.
Unlike the recently discovered BLURtooth vulnerability that deals with how Bluetooth devices pair with one another, BLESA was found in the reconnection process. Reconnections occur when two BLE devices move out of range and then move back into range. Normally BLE devices check the cryptographic keys negotiated during the pairing process when reconnecting.
The research team found that the official BLE specification did not contain strong-enough language to describe the reconnection process properly leading to two systemic issues making their way into BLE software implementations.
The first deals with the fact that authentication during device reconnection is optional as opposed to mandatory while the second relates to how authentication can potentially be circumvented if a user's BLE device fails to force another device to authenticate the cryptographic keys sent while reconnecting.
Why this matters:
Billions of devices could be vulnerable to these BLESA attacks where a nearby attacker bypasses reconnection verification and sends spoofed data to a BLE device with incorrect information. This can lead both humans and automated processes to make incorrect decisions when it comes to allowing two devices to reconnect with one another.
Coffee machines, cuddly toys and cars: The Internet of Things devices that could put you at risk from hackers
Connected teddy bears, connected coffee machines and connected cars are just some of the unusual Internet of Things (IoT) devices being insecurely connected to corporate networks that could leave whole organisations open to cyber attacks.
A research paper by Palo Alto Networks details the surge in IoT devices being connected to corporate networks and their wide variety.
Some of the most common irregular devices being connected to organisations' networks include connected vehicles, connected toys and connected medical devices, with connected sports equipment such as fitness trackers, gaming devices and connected cars also being deployed.
These devices are being connected because they can often help people through the working day or help manage aspects of their personal life, but they're also creating additional problems for the corporate network.
Why this matters:
In many cases, these 'shadow IoT' devices are being added to the network without the knowledge of the security team.
This could potentially leave the corporate network vulnerable because not only do some IoT devices have poor security that means they can easily be discovered and exploited, but some workplaces still have flat networks and if a device is compromised then an attacker can move from the IoT product to another system.
DDoS Attacks Skyrocket as Pandemic Bites
More people being online during lockdowns and more people working from home has proven to be lucrative for DDoS type attacks.
The first half of 2020 saw a significant uptick in the number of distributed denial-of-service (DDoS) attacks compared to the same period last year — a phenomenon that appears to be directly correlated to the global coronavirus pandemic.
One firm’s Security Operations Centre (SOC) saw a 151 percent increase in DDoS activity in the period, including one of the largest and longest attacks they had has ever mitigated – that attack came in at 1.17 terabits-per-second (Tbps), and lasted five days and 18 hours.
These figures are representative of the growing number, volume and intensity of network-type cyber attacks as organizations shifted to remote operations and workers’ reliance on the internet increased.
Why this matters:
DDoS attacks are getting bigger, with a “noticeable spike” in volume: The number of attacks sized 100Gbps and above grew a whopping 275 percent. Emblematic of this is a 2.3Tbps attack targeting an Amazon Web Services client in February – the largest volumetric DDoS attack on record. And the aforementioned 1.17Tbps attack was 192 percent bigger than the largest attack mitigated during the first half of 2019.
Read more: https://threatpost.com/ddos-attacks-skyrocket-pandemic/159301/
US charges two Russians for stealing $16.8m via cryptocurrency phishing sites
The US Department of Justice has filed charges this week against two Russian nationals for orchestrating a multi-year phishing operation against the users of three cryptocurrency exchanges.
The two suspects stand accused of creating website clones for the Poloniex, Binance, and Gemini cryptocurrency exchanges, luring users on these fake sites, and collecting their account credentials. These phishing operations began around June 2017.
US officials said the Russian duo — made up of Danil Potekhin (aka cronuswar) and Dmitrii Karasavidi; residents of Voronezh and Moscow, respectively — used the stolen credentials to access victim accounts and steal their Bitcoin (BTC) and Ether (ETH) crypto-assets.
Why this matters:
In total, US officials estimated the victims in the hundreds. Court documents cite 313 defrauded Poloniex users, 142 Binance victims, and 42 users at Gemini. Losses were estimated at $16,876,000.
Whilst bitcoin has waned in popularity after its highs a few years back there is still value in holdings held in different exchanges and these holdings remain popular targets for attackers.
US charges two Iranian hackers for years-long cyber-espionage, cybercrime spree
The US has also filed charges against and is seeking the arrest of two Iranian nationals believed to have carried out cyber-intrusions at the behest of the Iranian government and for their own personal financial gain.
In an indictment unsealed this week, prosecutors accused Hooman Heidarian and Mehdi Farhadi, both from Hamedan, Iran, of launching cyber-attacks against a wide range of targets since at least 2013.
Past victims included several US and foreign universities, a Washington think tank, a defense contractor, an aerospace company, a foreign policy organization, non-governmental organizations (NGOs), non-profits, and foreign government and other entities the defendants identified as rivals or adversaries to Iran, with most targets located in the US, Israel, and Saudi Arabia.
US officials said Heidarian and Farhadi focused on gaining access to their victims' accounts, computers, and internal networks, from where they stole confidential data and communications pertaining to topics such as national security, foreign policy, nuclear energy, and aerospace.
Why this matters:
Financial data and personally identifiable information wasn't off-limits, and the two also stole intellectual property, such as unpublished scientific research.
In addition, the two also targeted and stole personal information and communications of Iranian dissidents, human rights activists, and opposition leaders, according to George M. Crouch Jr., Special Agent in Charge of the FBI Newark Division.
Prosecutors believe that some of the stolen data was handed over to Iranian government intelligence officials, but that other information was also sold on black markets for the hackers' personal gains.
Alert issued to UK universities and colleges about spike in cyber attacks
British universities and colleges have been warned about a spike in ransomware attacks targeting the education sector by the UK's National Cyber Security Centre (NCSC), a part of GCHQ.
Academic institutions are being urged to follow NCSC guidance following a sharp increase in attacks which have left some teachers fearing they won't be able to accept students when term begins.
Last week staff at Newcastle University warned Sky News they had "no idea how we are going to welcome students in three weeks' time" following one such ransomware attack, which has impacted IT services across the whole university.
Similar attacks in which criminal hackers infiltrated computer networks and stole data before encrypting the machines and demanding a ransom payment to unlock them again, have hit Northumbria University, Bolton Sixth Form College, Leeds City College and others in August alone.
Speaking to Sky News, NCSC's director of operations Paul Chichester said the agency had seen an increase in the "utterly reprehensible" attacks over the past 18 months and was concerned they would disrupt young people's education.
Why this matters:
There are more than a dozen criminal groups which are currently earning millions by encrypting their victim's computer networks and then leaking stolen documents online to pressure the victims into paying up.
The Most Effective Phishing Lures - which ones will you fall for...?! Cyber Tip Tuesday video 15 September 2020
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week Tony is talking about the most effective phishing lures.
Which phishing emails subject lines or hooks are user most likely to fall for?
Phishing emails often have a sense of urgency attached to them to get users to react without taking time to think or assess whether the email is genuine, but there are also subject lines that are more likely to trick users.
Anything where the user things they may be about to lose something they have earned or are entitled to can be effective, so things like a change or reduction in pay or benefits, reduction in holidays or a loss of things like airmiles or hotel loyalty points can be effective.
Anything involving threats of criminal action, courts, or implying you will incur a cost or charge for not complying is also effective, especially when combined with the sense of urgency.
Make sure your users are aware of the most effective lures and are continually honing their ability to spot phishing emails with rolling testing.
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week Tony is talking about the most effective phishing lures.
Which phishing emails subject lines or hooks are user most likely to fall for?
Phishing emails often have a sense of urgency attached to them to get users to react without taking time to think or assess whether the email is genuine, but there are also subject lines that are more likely to trick users.
Anything where the user things they may be about to lose something they have earned or are entitled to can be effective, so things like a change or reduction in pay or benefits, reduction in holidays or a loss of things like airmiles or hotel loyalty points can be effective.
Anything involving threats of criminal action, courts, or implying you will incur a cost or charge for not complying is also effective, especially when combined with the sense of urgency.
Make sure your users are aware of the most effective lures and are continually honing their ability to spot phishing emails with rolling testing.
Cyber Weekly Flash Briefing 11 September 2020: Ransomware 41% of H1 2020 cyber insurance claims, MS Critical RCE Bugs, 60% of emails May/June fraudulent, Insider Data Breaches, Linux Targeting More
Cyber Weekly Flash Briefing 11 September 2020: Ransomware 41% of all H1 2020 cyber insurance claims, MS Patch Tuesday Critical RCE Bugs, 60 percent of emails May/ June were fraudulent, Insider-Enabled Data Breaches, Linux-Based Devices Targeted More, Chilean bank shut down following ransomware, meddling in US politics by Russia, China & Iran, TikTok battles to remove video of livestreamed suicide
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Ransomware accounted for 41% of all cyber insurance claims in H1 2020
Ransomware incidents have accounted for 41% of cyber insurance claims filed in the first half of 2020, according to a report published today by one of the largest providers of cyber insurance services in North America.
The high number of claims comes to confirm previous reports from multiple cyber-security firms that ransomware is one of today's most prevalent and destructive threats.
Ransomware doesn't discriminate by industry. An increase in ransom attacks has been seen across almost every industry.
In the first half of 2020 alone, they observed a 260% increase in the frequency of ransomware attacks amongst their policyholders, with the average ransom demand increasing 47%.
Among the most aggressive gangs, the cyber insurer listed Maze and DoppelPaymer, which have recently begun exfiltrating data from hacked networks, and threatening to release data on specialized leak sites, as part of double extortion schemes.
Why this matters:
Ransomware remains, and is likely to remain, by far one of the biggest menaces on the web, it is indiscriminate, anyone can be affected, it can be business destroying, and it is getting worse all the time.
Read more: https://www.zdnet.com/article/ransomware-accounts-to-41-of-all-cyber-insurance-claims/
Microsoft’s Patch Tuesday Packed with Critical RCE Bugs
Microsoft has released patches for 129 security bugs in its September Patch Tuesday update. These include 23 critical flaws, 105 that are important in severity and one moderate bug. Fortunately, none are publicly known or under active exploitation, Microsoft said.
The most severe issue in the bunch is CVE-2020-16875, according to researchers. This is a memory-corruption problem in Microsoft Exchange that allows remote code-execution (RCE) just by sending an email to a target. Running arbitrary code could grant attackers the access they need to create new accounts, access, modify or remove data, and install programs.
Why this matters:
Many organisations are struggling to keep up with the volume of updates and keeping on top of them, or knowing which to prioritise, is critical for firms. At a time while many organisations continue to struggle to support the ongoing distribution of remote workers, Microsoft continues to pile on the updates and finding an efficient method for rolling out these patches has become even more imperative as companies begin to abandon the idea of a short-term fix and shift operations to embrace remote work as part of a lasting, long-term progression of how organisations operate moving forward.
Firms are beginning to realise the negative outcomes of the lenient security measures put in place to quickly adapt to a decentralised workforce and it’s become more important than ever to establish patching policies that can securely support remote endpoints for the foreseeable future.
Read more: https://threatpost.com/microsofts-patch-tuesday-critical-rce-bugs/159044/
60 percent of emails in May and June were fraudulent
The COVID-19 pandemic has seen a spike in scams, phishing and malware across all platforms and attack vectors. The latest mid-year threat landscape report from Bitdefender shows that in May and June, an average of 60 percent of all received emails were fraudulent.
In addition there’s been a five-fold increase in the number of coronavirus-themed attacks and a 46 percent increase in attacks aimed at home IoT devices.
IoT malware has become versatile, robust, and is constantly updated. IrcFlu, Dark_Nexus7 and InterPLanetary Storm are some of the examples malware that gained in popularity during the first half of 2020.
Mobile malware has been quick to capitalise too, with malware developers rushing to weaponise popular applications, such as the Zoom video conferencing application, used by employees now working from home. Packing RAT (Remote Access Trojan) capabilities, or bundling them with ransomware, banking malware, or even highly aggressive adware, Android malware developers were also fully exploiting the pandemic wave.
Why this matters:
As we keep saying malicious actors never let a good crisis or tragedy go to waste and will exploit whatever is going on in the world or anything there is a collective interest in to real in unsuspecting victims.
Good awareness and education are key in keeping your employees and users safe and ensuring users at all levels, including board members – who present a significant risk, are up to date with latest tactics and threats.
Email in particular will remain primary vector for attack and this is unlikely to change any time soon.
Read more: https://betanews.com/2020/09/08/60-percent-of-emails-in-may-and-june-were-fraudulent/
Businesses [should] Fear Insider-Enabled Data Breaches
Businesses fear suffering a data breach and expect it to be caused by an insider or internal error.
A survey of 500 IT professionals found that 94% of respondents have experienced a data breach, and 79% were worried their organisation could be next.
The fear associated with breaches stems from the security culture within the organisation, along with the security reporting structure.
Having security teams in close dialogue with executive leadership, supporting the leadership to make informed risk-based decisions and driving the business strategy, including the technologies used, reduces this fear significantly.
Secondly, not understanding information security, its components and principles drives fear and anxiety of the unknown, so having security education training, and developing awareness and consciousness of threats, will enable and empower the entire organisation to act with a ‘security first’ mindset.
Finally, recognising the importance of access control to protect systems and data is a foundational level control that organisations can apply to reduce the risk of a data breach. Hand in hand with this is partnering with trusted identity and access control platform providers who can provide enterprises with that security expertise and industry leadership.
Why this matters:
In terms of what is causing the breaches, 40% of respondents to the survey said accidental employee incidents were to blame, compared to 21% who said it is external attackers. Asked if this is a case of businesses not having a handle on what leaves their organisations (either intentionally or accidentally), insiders already have access and can leave with data invisibly, which might turn up somewhere embarrassing later.
Read more: https://www.infosecurity-magazine.com/news/businesses-insider-breaches/
4 top vulnerabilities ransomware attackers exploited in 2020
As more employees work from home, attackers have more endpoints to target. These unpatched vulnerabilities in remote access tools and Windows makes their job easier.
The biggest security trend for 2020 has been the increase of COVID-19-related phishing and other attacks targeting remote workers. New York City, for example, has gone from having to protect 80,000 endpoints to around 750,000 endpoints in its threat management since work-from-home edicts took place.
As noted in a recent Check Point Software Technologies mid-year review, “The first impact of the pandemic was the proliferation of malware attacks that used social engineering techniques with COVID-19 thematic lures for the delivery stage.” Domain names were set up and parked with names relating to the pandemic. As workers started to use videoconferencing platforms, attacks moved to attacking Zoom, Teams and other videoconferencing platforms.
One disturbing trend is that 80% of the observed attacks in the first half of 2020 used vulnerabilities reported and registered in 2017 and earlier, according to the Check Point report, and more than 20% of the attacks used vulnerabilities that are at least seven years old. This showcases that we have a problem in keeping our software up to date.
Why this matters:
Ransomware remains a big threat 2020 and expanding attack surfaces with staff working from home is making the situation worse. Attackers use vulnerabilities in tools used for remote access into Windows networks.
Click read more below to find out the top four vulnerabilities the researchers identified.
APT Groups Increasingly Targeting Linux-Based Devices
APT groups are increasingly executing targeted attacks against Linux-based devices as well as developing more Linux-focused tools, according to an investigation by Kaspersky.
This is as a result of a growing number of organisations’ selecting Linux ahead of Windows to run their strategically important servers and systems, and the perception that the Linux operating system is safer and less likely to be targeted by malware as it is less popular.
However, threat-actors have been observed to adapt their tactics to take advantage of this trend, and Kaspersky noted that “over a dozen APT actors have been observed to use Linux malware or some Linux-based modules” during the past eight years.
These include notorious groups such as Turla, Lazarus, Barium, Sofacy, the Lamberts and Equation. Kaspersky highlighted the example of Russian speaking APT group Turla using Linux backdoors as part of its changing toolset in recent years.
Why this matters:
Attacks that target Linux-based systems are still fewer in number than attacks on Windows based systems, but there is still malware designed to target them, including webshells, backdoors, rootkits and even custom-made exploits.
Read more: https://www.infosecurity-magazine.com/news/apt-targeting-linux-based-devices/
Major Chilean bank shuts down all branches following ransomware attack
Banco Estado, the only public bank in Chile and one of the three largest in the country, had to shut down its nationwide operations on Monday due to a cyberattack that turned out to be a ransomware launched by REvil.
According to a public statement, the branches will remain closed for at least one day, but clarified that customers’ funds have not been affected by the incident.
Sources close to the investigation reported that the REvil ransomware gang is behind the attack. It reportedly originated from an Office document infected with the malware that an employee received and proceeded to open.
The incident was reported to the Chilean authorities, who issued a cyber-security alert that warned about a massive ransomware campaign targeting the private sector in the country.
Why this matters:
As above ransomware is not going away and is getting worse all the time. Too many users don’t realise that simply opening a document or clicking on a link in an email could bring down their entire organisations. Staff and users need to be educated about the role they play in securing their organisations.
Vulnerabilities discovered in PAN-OS, which powers Palo Alto Networks’ firewalls
Palo Alto Networks this week remediated vulnerabilities in PAN-OS (operating systems version 8.1 or later) which command injection, cross site scripting and the ability to upload unauhtoised files to a directory which might lead to denial of service.
Why this matters:
Attackers can use these vulnerabilities to gain access to sensitive data or develop the attack to gain access to the internal segments of the network of a company that uses vulnerable protection tools.
Any security fixes for known vulnerabilities across any different product, software or firmware should be tested and applied as soon as possible, so those vulnerabilities cannot be used against you or your organisation.
Read more: https://www.helpnetsecurity.com/2020/09/10/vulnerabilities-discovered-in-pan-os/
Russia, China and Iran hackers target Trump and Biden, Microsoft says
Hackers with ties to Russia, China and Iran are attempting to snoop on people and groups involved with the US 2020 presidential election, Microsoft says.
The Russian hackers who breached the 2016 Democratic campaign are again involved, said the US tech firm.
Microsoft said it was "clear that foreign activity groups have stepped up their efforts" targeting the election.
Both President Donald Trump and Democrat Joe Biden's campaigns are in the cyber-raiders' sights.
Russian hackers from the Strontium group have targeted more than 200 organisations, many of which are linked to US political parties - both Republicans and Democrats, Microsoft said in a statement.
Why this matters:
The same attackers have also targeted British political parties, said Microsoft, without specifying which ones. Any meddling in politics by foreign states is a clear threat to the democratic process and shows that unfriendly states will interfere to further their own agendas.
Read more: https://www.bbc.co.uk/news/world-us-canada-54110457
TikTok battles to remove video of livestreamed suicide
TikTok is battling to remove a graphic video of a livestreamed suicide, after the footage was uploaded to the service on Sunday night from Facebook, where it was initially broadcast.
Although the footage was rapidly taken down from TikTok, users spent much of Monday re-uploading it, initially unchanged, but later incorporated into so-called bait-and-switch videos, which are designed to shock and upset unsuspecting users.
One such video, for instance, begins with a conventional video of an influencer talking to camera, before cutting without warning to the graphic footage.
Why this matters:
Parents, especially of younger children, may think that certain sites and social media channels are safe for children and the content is suitable vetted and controlled, but as this illustrates that is often not the case and caution should be exercised in allow young children unfettered access to social media.
Two for one - Red Arrows and a neighbouring Pride flag
Two for one - Red Arrows and a neighbouring Pride flag
Beautiful day for it
Black Arrow is proud to be one of the sponsors for this weekend's Channel Island's Pride
Black Arrow is proud to be one of the sponsors for this weekend's Channel Island's Pride
One of the only Pride events to be happening across the British Isles, and hopefully the weather will hold for Saturday. We hope everyone attending has a fantastic day
Lessons from Charities and Upcoming Charities Workshop this Thursday
Welcome to this week's Black Arrow Cyber Tip Tuesday.
This week, Black Arrow will host a workshop on cyber security for charities. This is part of our pro-bono work with charities and the Guernsey Community Foundation.
As research, we have worked with a few charities to look at their main information and cyber security risks, and the solutions that they can implement either free of charge or at low cost.
We have seen that a charity is effectively a small business, where the team uses information that needs to be safeguarded. But a charity’s information can be very confidential where it relates to the health or private lives of its members.
The charity’s team, including employees and volunteers, might not be aware of information security or be at ease using technology. For example, employees and volunteers often receive sensitive information at home using their own computer, and then download it onto that computer and print it out to take with them when visiting the member.
There is sometimes no control over what happens to that sensitive printed document and how it is stored or disposed of.
Equally, the charity’s employees and volunteers need to be alert to the risks of using online technology and the tactics of criminals who try to get access to their computer and information.
At the workshop, we will be looking at these risks and ways to improve information and cyber security at no cost or low cost. For more information, visit the Guernsey Community Foundation website or our website blackarrowcyber.com. And contact us if you would like to be part of our pro-bono work.
If you are a charity and would like to attend Thursday's free workshop email joni@foundation.gg to book your place
Welcome to this week's Black Arrow Cyber Tip Tuesday.
This week, Black Arrow will host a workshop on cyber security for charities. This is part of our pro-bono work with charities and the Guernsey Community Foundation.
As research, we have worked with a few charities to look at their main information and cyber security risks, and the solutions that they can implement either free of charge or at low cost.
We have seen that a charity is effectively a small business, where the team uses information that needs to be safeguarded. But a charity’s information can be very confidential where it relates to the health or private lives of its members.
The charity’s team, including employees and volunteers, might not be aware of information security or be at ease using technology.
For example, employees and volunteers often receive sensitive information at home using their own computer, and then download it onto that computer and print it out to take with them when visiting the member.
There is sometimes no control over what happens to that sensitive printed document and how it is stored or disposed of.
Equally, the charity’s employees and volunteers need to be alert to the risks of using online technology and the tactics of criminals who try to get access to their computer and information.
At the workshop, we will be looking at these risks and ways to improve information and cyber security at no cost or low cost.
For more information, visit the Guernsey Community Foundation website (foundation.gg) or our website blackarrowcyber.com. And contact us if you would like to be part of our pro-bono work.
If you are a charity and would like to attend Thursday's free workshop email joni@foundation.gg to book your place
Cyber Weekly Flash Briefing 04 September 2020: CEOs could become personally liable for cyber attacks, DDoS extortion, WordPress flaw exploited, Business Email Compromise now $80k, printers at risk
Cyber Weekly Flash Briefing 04 September 2020: CEOs could soon be personally liable for cyber attacks, DDoS Extorters Demand Ransoms from Firms, Hackers exploiting a critical WordPress flaw, Average Business Email Compromise (BEC) attempts are now $80k, Iran based Pioneer Kitten APT Sells Corporate Network Access, Nearly A Million Printers At Risk Of Attack - Thousands Hacked To Prove It
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
CEOs could soon be personally liable for cyberattacks
Within four years, the majority of CEOs will be held personally responsible for cyberattacks that lead to injury and other physical damage.
This is according to a new report from Gartner, which asserts that liability for cyber-physical security incidents will “pierce the corporate veil to personal liability” for 75 percent of CEOs by 2024.
Cyber-physical systems (CPS) are described as digital systems that interact with the physical world, such as IoT devices or operational technologies (OT).
“Regulators and governments will react promptly to an increase in serious incidents resulting from failure to secure CPSs, drastically increasing rules and regulations governing them,” said Katell Thielemann, Research Vice President at Gartner.
“In the US, the FBI, NSA and Cybersecurity and Infrastructure Security Agency (CISA) have already increased the frequency and details provided around threats to critical infrastructure-related systems, most of which are owned by private industry. Soon, CEOs won’t be able to plead ignorance or retreat behind insurance policies.”
Why this matters:
CPS attacks with fatalities will incur costs to businesses of more than $50 billion within the next three years, Gartner predicts. Irrespective of the value of human life, businesses are looking at major costs in terms of compensation, litigation, insurance, regulatory fines and reputation loss.
Technology leaders need to help CEOs understand the risks that CPSs represent and the need to dedicate focus and budget to securing them. The more connected CPSs are, the higher the likelihood of an incident occurring.
Read more: https://www.itproportal.com/news/ceos-could-soon-be-personally-liable-for-cyberattacks/
Global DDoS Extorters Demand Ransom from Firms
Security experts are warning of a new global DDoS-related extortion campaign targeting businesses operating in the e-commerce, finance and travel sectors.
Researchers said they had been tracking the threat actors since mid-August, with victims in North America, APAC and EMEA. Emails are typically delivered claiming to come from state-sponsored groups such as Fancy Bear and Lazarus Group, as well as the “Armada Collective.”
The latter group has been linked to similar extortion emails sent in previous years.
The ransom emails threaten to launch DDoS attacks against the recipient organization of over 2Tbps, if payment of anywhere between 10 and 20BTC ($113,000-226,000) is not made. They also threaten to increase the ransom by 10BTC for each deadline missed.
Also included in the messages are the Autonomous System Numbers (ASNs) or IP addresses of servers or services that the group says it will target if their demands are not met.
Why this matters:
DDoS attacks take businesses legitimate online operations offline by flooding them with traffic such that legitimate traffic can’t get through, or they are so swamped with traffic that services can’t cope. Depending on the type of business and how reliant they are on their online presence these types of attacks could prevent firms from operating entirely.
Recipients of the emails were urged not to pay the ransom
Read more: https://www.infosecurity-magazine.com/news/global-ddos-extorters-ransom-notes/
Hackers are exploiting a critical flaw affecting >350,000 WordPress sites
Hackers are actively exploiting a vulnerability that allows them to execute commands and malicious scripts on Websites running File Manager, a WordPress plugin with more than 700,000 active installations, researchers said on Tuesday. Word of the attacks came a few hours after the security flaw was patched.
Why this matters:
Attackers are using the exploit to upload files hidden in an image, which from there provides a convenient interface that allows them to run commands in the directory where the File Manager plugin resides. Hackers may be able to exact more damage by uploading scripts that can carry out actions on other parts of a vulnerable site.
Phishing attacks surge during the pandemic
In yet another example of cyber criminals exploiting world events, the frequency of phishing threats has risen considerably since the start of the pandemic, with companies experiencing an average of 1,185 attacks every month.
New research reveals that more than half (53 percent) of over 300 IT professionals surveyed by Cyber security Insiders say they had witnessed an increase in phishing activity since the start of the COVID-19 pandemic.
Why this matters:
The report also shows that 38 percent of respondents report that a co-worker has fallen victim to an attack within the last year. As a result, 15 percent of organizations are now left spending anywhere from one to four days remediating malicious attacks during what is already a difficult time for many.
Read more: https://betanews.com/2020/09/01/phishing-surges-during-pandemic/
Average Business Email Compromise (BEC) attempts are now $80k, but one group is aiming for $1.27m per attack
BEC scammer groups are growing more brazen. The average sum that a BEC group will try to steal from a targeted company is now around $80,000 per attack, according to an industry report published on Monday.
The number is up from $54,000, the average sum that BEC groups tried to obtain from victims in Q1 2020, as reported by the Anti-Phishing Working Group (APWG), an industry coalition made up of more than 2,200 organizations from the cyber-security industry, government, law enforcement, and NGOs sector.
One of the largest industry group of its kind, the APWG has been releasing quarterly reports on the state of phishing operations since 2004.
Why this matters:
Most of these reports have usually centred on email phishing attacks that focus on stealing login credentials and distributing malware. However, since the mid-2010s, BEC fraud has been slowly taking more and more space in APWG's reports, as BEC fraud has become today's top cybercrime trend.
BEC, or Business Email Compromise (BEC) scams, usually begin with phishing, with an email sent to a company's employee. The end goal is to dupe the employee into paying fake invoices or transferring funds to an account controlled by the attackers.
Iran based Pioneer Kitten APT Sells Corporate Network Access
An APT (Advanced Persistent Threat) group known as Pioneer Kitten, linked to Iran, has been spotted selling corporate-network credentials on hacker forums.
Pioneer Kitten is a hacker group that specialises in infiltrating corporate networks using open-source tools to compromise remote external services. Researchers observed an actor associated with the group advertising access to compromised networks on an underground forum in July, according to a blog post earlier this week.
Pioneer Kitten’s work is related to other groups either sponsored or run by the Iranian government, which were previously seen hacking VPNs and planting backdoors in companies around the world.
Why this matters:
The credentials would let other cybercriminal groups and APTs perform cyberespionage and other nefarious cyber-activity. It is also noteworthy to see a group operating on behalf of or closed with a Nation State, in this case Iran, appearing to potential attempt to diversify their revenue streams through sales of stolen credentials.
Read more: https://threatpost.com/pioneer-kitten-apt-sells-corporate-network-access/158833/
Nearly A Million Printers At Risk Of Attack, Thousands Hacked To Prove It
Roughly 28,000 printers recently gave their owners an unexpected lesson in cybersecurity. Seemingly unprompted, the printers whirred to life and produced a 5-step guide to keeping hackers at bay.
“This printer has been hacked,” the message began ominously. Fortunately for the “victims” it was a group of ethical hackers behind the attack. A team of researchers from CyberNews was out to remind the public about the potential peril of connected devices.
To get the ball rolling, the team scoured the globe for printers that were vulnerable. They found more than 800,000 in total using a search engine called Shodan.
Shodan is a tool that’s leaned on by both security researchers and cyber criminals. In the past it’s been used to identify thousands of at-risk surveillance cameras, security alarm systems and hundreds of wind turbines and solar devices.
Why this matters:
Vulnerable devices within your networks can present a vulnerability to other devices on your network too and can be an easy point of entry for attackers.
Many firms do a good job of updating desktops and laptops when operating system updates come out, but too many firms neglect networking devices such as routers, modems and switches, and other devices on their networks such as printers.
Read more: https://www.forbes.com/sites/leemathews/2020/08/31/800000-printers-vulnerable-28000-hacked/#4b7c9b87d8a9
or: https://cybernews.com/security/we-hacked-28000-unsecured-printers-to-raise-awareness-of-printer-security-issues/
WhatsApp reveals six previously undisclosed vulnerabilities on new security site
Facebook -owned WhatsApp has revealed six previously undisclosed vulnerabilities, which the company has now fixed. The vulnerabilities are being reported on a dedicated security advisory website that will serve as the new resource providing a comprehensive list of WhatsApp security updates and associated Common Vulnerabilities and Exposures (CVE).
WhatsApp said five of the six vulnerabilities were fixed in the same day, while the remaining bug took a couple of days to remediate. Although some of the bugs could have been remotely triggered, the company said it found no evidence of hackers actively exploiting the vulnerabilities.
Why this matters:
WhatsApp is one of the world’s most popular apps, with more than two billion users around the world. But it’s also a persistent target for hackers, who try to find and exploit vulnerabilities in the platform. As with all software updates should be applied as soon as possible to ensure that fixes that remediate known vulnerabilities are fixed.
Read more: https://techcrunch.com/2020/09/03/whatsapp-security-flaws/
Attackers are trying to exploit a high-severity zero day in Cisco gear
Telecoms and data-centre operators take note: attackers are actively trying to exploit a high-severity zero day vulnerability in Cisco networking devices, the company warned over the weekend.
The security flaw resides in Cisco’s iOS XR Software, an operating system for carrier-grade routers and other networking devices used by telecommunications and data-centre providers. In an advisory published on Saturday, the networking-gear manufacturer said that a patch is not yet available and provided no timeline for when one would be released.
Why this matters:
Zero days do not yet have patches available although the vulnerability is publicly known and in some cases, as in this case, already being targeted by malicious actors.
Cyber and Information Security Lessons from the Titanic Disaster
On the day the Titanic sank the crew received 7 iceberg warnings, yet such was the competition to make the crossing in 6 days orders were given to maintain the speed of the ship in the mistaken belief they could carry on unaffected.
Now if the crew had heeded the warnings to slow down they would have stood a much better chance of avoiding the icebergs and in particular of course the iceberg that led to their sinking.
That's not to say good security means you need to slow down.
Whilst not wishing to mix metaphors brakes were not added to cars to make them go slower, quite the opposite - brakes were needed to allow cars to go faster.
Just maybe don't ignore the warnings in the belief that somehow you will remain unaffected as you sail you own ships through seas unfortunately filled with icebergs.
Contact us to see how we can help you steer your ships and stay safe as you do business in an increasingly connected world
On the day the Titanic sank the crew received 7 iceberg warnings, yet such was the competition to make the crossing in 6 days orders were given to maintain the speed of the ship in the mistaken belief they could carry on unaffected.
Now if the crew had heeded the warnings to slow down they would have stood a much better chance of avoiding the icebergs and in particular of course the iceberg that led to their sinking.
That's not to say good security means you need to slow down.
Whilst not wishing to mix metaphors brakes were not added to cars to make them go slower, quite the opposite - brakes were needed to allow cars to go faster.
Just maybe don't ignore the warnings in the belief that somehow you will remain unaffected as you sail you own ships through seas unfortunately filled with icebergs.
Contact us to see how we can help you steer your ships and stay safe as you do business in an increasingly connected world
Cyber Weekly Flash Briefing 28 August 2020: cyber crime cost per minute $11.4m by 2021, Trend block 28 billion Cyber Threats H1 2020, Malicious Attachments Top Threat, NK hackers ramp up bank heists
Cyber Weekly Flash Briefing 28 August 2020: global cost of cybercrime per minute to reach $11.4 million by 2021, Trend blocks 28 Billion Cyber-Threats in H1 2020, Malicious Attachments Remain a Cyber Criminal Threat Vector Favourite, 80% of Exploits Published Faster than CVEs, North Korean hackers ramp up bank heists
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
The global cost of cyber crime per minute to reach $11.4 million by 2021
Cyber crime costs organisations $24.7, YOY increase of more than $2 every minute, according to a new report. It will also have a per-minute global cost of $11.4 million by 2021, a 100% increase over 2015.
The report covers the top threats facing today’s organizations, which are proliferating at a clip of 375 per minute, and reflects the current surge in attacks leveraging the COVID-19 pandemic.
Other malicious activity
1.5 attacks on computers with an Internet connection per minute
375 new threats per minute
16,172 records compromised per minute
1 vulnerability disclosed every 24 minutes
5.5 vomain infringements detected per minute
1 Magecart attack every 16 minutes
1 COVID-19 blacklisted domain every 15 minutes
35 COVID-19 spam emails analysed per minute
Why this matters:
The sheer scale of today’s threat activity is driven by a variety of factors, including that cyber crime is easier than ever to participate in and better threat technology makes cyber criminals more effective and wealthier than in the past.
Read more: https://www.helpnetsecurity.com/2020/08/28/global-cost-of-cybercrime-per-minute/
Trend Micro Blocks 28 Billion Cyber-Threats in H1 2020
Trend Micro blocked nearly nine million COVID-related threats in the first half of 2020, the vast majority of which were email-borne, it revealed in a new mid-year roundup report.
The security giant said it detected 8.8 million cyber-threats leveraging the virus as a lure or theme for attacks, 92% of which were delivered by spam emails.
However, the figure represents less than 1% of the total of 27.8 billion threats the vendor blocked in the first six months of the year.
This chimes with data from Microsoft and others which suggests that cyber-criminals merely repurposed existing campaigns to take advantage of COVID-19. As such, the pandemic itself has not prompted a rise in overall cyber crime levels.
However, the data does show conclusively that email remains the number one threat vector: 93% of total blocked threats were heading for users’ inboxes.
As part of this trend, Business Email Compromise (BEC) detections increased by 19% from the second half of 2019. This is due in part to scammers trying to capitalize on distracted home workers who may be more exposed to social engineering, and less able to check with colleagues if a money transfer request is legitimate or not.
Why this matters:
Email remains the number one threat to all firms and by far the most likely way firms will end up being breached, and this depends on your users being aware and switched on and efficient at spotting email borne attacks as technology solutions alone are not good at blocking email based attacks. Criminals will always exploit current events and crises to improve their effectiveness of their attacks.
Read more: https://www.infosecurity-magazine.com/news/trend-micro-blocks-28-billion/
Malicious Attachments Remain a Cyber Criminal Threat Vector Favourite
Malicious attachments continue to be a top threat vector in the cybercriminal world, even as public awareness increases and tech companies amp up their defences.
While attachment threat vectors are one of the oldest malware-spreading tricks in the books, email users are still clicking on malicious attachments that hit their inbox, whether it’s a purported “job offer” or a pretend “critical invoice.”
The reason why threat actors are still relying on this age-old tactic, researchers say, is that the attack is still working. Even with widespread public awareness about malicious file attachments, attackers are upping their game with new tricks to avoid detection, bypass email protections and more. The attack vector is still widespread enough where tech giants are re-inventing new ways to try to stomp it out, with Microsoft just this week rolling out a feature for Office 365 that aims to protect users against malicious attachments sent via email, for instance.
Why this matters:
Email attachments, such as PDF or Office files, are an easy vector to deliver malicious content to end users. For enterprises, the risk is that malicious actors can use these attachments to establish a toe-hold at the outermost edges of the enterprise, and then wait and wind their way to the crown jewels in their data stores.
Read more here: https://threatpost.com/malicious-attachments-remain-a-cybercriminal-threat-vector-favorite/158631/
The State of Exploit Development: 80% of Exploits Publish Faster than CVEs
With the ever-increasing number of new vulnerabilities, vulnerability management becomes one of the most critical processes in ensuring continuous business operation. While it is clear that timely patching is essential, it’s also important to know quantitatively how a delay could increase risk. What are the chances that attackers breach an organisation using a CVE just disclosed or using an unknown (zero-day) vulnerability? To understand the state of vulnerability disclosure and exploit development, researchers analysed 45,450 the publicly available exploits in the Exploit Database at the time of this writing. The research correlated the exploit data with vulnerability and patch information to study exploit development in multiple facets.
The research reveals that:
Of the 45,450 public exploits in Exploit Database, there are 11,079 (~26%) exploits in Exploit Database that have mapped CVE numbers.
Among those 11,079 exploits:
14% are zero-day (published before the vendors release the patch), 23% are published within a week after the patch release and 50% are published within a month after the patch release. On average, an exploit is published 37 days after the patch is released. Patch as soon as possible – the risk of a vulnerability being exploited increases quickly after vendors release the patches.
80% of public exploits are published before the CVEs are published. On average, an exploit is published 23 days before the CVE is published. Software and hardware may also have vulnerabilities with public exploits that don’t have CVEs. Check security updates from vendors frequently and apply updates as soon as possible.
Analysis of the entire CVE list since 1999 found that, on average, a CVE is published 40 days after its CVE-ID is assigned. Of the 177,043 entries analysed more than 10,000 CVEs have been in “reserved” status for more than two years. It shows that there is a long delay between vulnerability discovery and CVE publication.
Why this matters:
Patches should always be applied as soon as possible, exploits either follow very soon after vulnerability disclosure but as this study shows sometimes vulnerabilities are being exploited before fixes are released. The longer between fixes being released and being applied the more vulnerable you are to attack.
Read more here: https://unit42.paloaltonetworks.com/state-of-exploit-development/
Forget your space-age IT security systems. It might just take a $1m bribe and a willing employee to be pwned
A Russian citizen is accused of flying to America in a bid to bribe a Tesla employee to infect their bosses' IT network with ransomware.
Egor Kriuchkov has been charged with one count of conspiracy to intentionally cause damage to a protected computer. He was nabbed by the Feds at Los Angeles airport and is behind bars awaiting trial.
It is claimed Kriuchkov, 27, was the point man of a plot to get data-stealing malware onto the network of an unspecified US company in Nevada and then use the lifted data to extort the corporation for millions of dollars: paid up, or the internal files get leaked and file systems scrambled.
To do this, Kriuchkov and his associates back in Russia had recruited a worker at the business, it is claimed, and promised to pay $500,000 for placing the malware onto its network. The bribe was later increased to $1m to persuade the employee, along with an $11,000 advance, yet instead he went to his bosses, and the FBI was brought in, we're told.
According special agent Michael Hughes, in late July Kriuchkov travelled from Russia to Reno, Nevada, where the employee worked, and over the early weeks of August tried to win over the employee to join the conspiracy. This included a night out for the worker and friends at a Lake Tahoe resort, followed by Kriuchkov pulling the worker aside and convincing them to play a key role in the operation, it is claimed.
Why this matters:
Again this shows that employees are more likely than your technical systems to be exploited by malicious actors, fortuitously for Tesla the employee didn’t take the bribe but many staff in different organisations would be tempted. Imagine if the employee that was approached was already feeling disgruntled against their employer.
Read more here: https://www.theregister.com/2020/08/26/russian_malware_plot/
Ex-Cisco staffer charged with deliberately deleting 400+ VMs
A disgruntled former Cisco employee has pleaded guilty to intentionally deleting hundreds of the networking firm's virtual machines (VMs), according to an IT News report.
Sudhish Kasaba Ramesh, an ex-Cisco engineer who left the company in April 2018, accessed the firm's AWS environment months later and deleted a total of 456 VMs, which the company used to run the WebEx Teams application.
In a statement, issued before a US federal court in San Jose by the US Department of Justice and the FBI, it was said that Ramesh “intentionally accessed a protected computer without authorization and recklessly caused damage”.
“During his unauthorized access, Ramesh admitted that he deployed a code from his Google Cloud Project account that resulted in the deletion of 456 virtual machines for Cisco’s WebEx Teams application, which provided video meetings, video messaging, file sharing, and other collaboration tools,” the statement said.
Why this matters:
Insiders will always be amongst the biggest threats to every organisation and the damage a disgruntled employee or former employer could cause should never be underestimated. Any time a member of staff leaves an organisation it must be ensured that they no longer have access to any accounts accessed in the course of the performing their duties, and doubly so for accounts with privileged or elevated permissions, for the very reason they could do so much damage.
Read more: https://www.itproportal.com/news/ex-cisco-staffer-charged-with-deliberately-deleting-400-vms/
North Korean hackers ramp up bank heists: U.S. government cyber alert
North Korean hackers are tapping into banks around the globe to make fraudulent money transfers and cause ATMs to spit out cash, the U.S. government warned on Wednesday.
A technical cyber security alert jointly written by four different federal agencies, including the Treasury Department and FBI, said there had been a resurgence in financially motivated hacking efforts by the North Korean regime this year after a lull in activity.
“Since February 2020, North Korea has resumed targeting banks in multiple countries to initiate fraudulent international money transfers and ATM cash outs,” the warning reads.
U.S. law enforcement titled the hacking campaign “Fast Cash” and blamed North Korea’s Reconnaissance General Bureau, a spy agency, for it. They described the operation as going on since at least 2016 but ramping up in sophistication and volume recently.
Why this matters:
Over the last several years, North Korea has been blamed by U.S. authorities and private sector cyber security companies for hacking numerous banks in Asia, South America and Africa.
North Korean cyber actors have demonstrated an imaginative knack for adjusting their tactics to exploit the financial sector as well as any other sector through illicit cyber operations.
Read more here: https://www.reuters.com/article/us-cyber-usa-north-korea-idUSKBN25M2FU
New Zealand stock exchange resumes trade after cyber attacks, government activates security systems
New Zealand’s stock exchange resumed trading on Friday, after facing disruptions for four consecutive days in the wake of cyber attacks this week, while the government said national security systems had been activated to support the bourse.
There is no clarity on who was behind these two “offshore” attacks, but the failure to stop them has raised questions about New Zealand’s security systems, experts said.
NZX Ltd had to halt trading until afternoon on Friday, after crashing earlier due to network connectivity issues, marking the fourth day that trading has been hit.
Why this matters:
Organisations of all sizes are vulnerable to attacks, larger firms are vulnerable because of the sheer number of users and the complexity of their systems, smaller firms because they often lack maturity and don’t have the most appropriate controls and protections in place. Firms also need to make sure they have plans in place to recover and return to operational effectiveness as quickly as possible.
Read more here: https://www.reuters.com/article/uk-nzx-cyber-idUSKBN25O03Q
The Dangers of Public Wi-Fi - Cyber Tip Tuesday video 25 August 2020
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week James is talking about public or insecure Wi-Fi.
Unsecured Public Wi-Fi is a minefield of security risks. If you're connecting to an unsecured access point or a network where the key is publicly available, such as an airport, coffee shop or public event then you're susceptible to a host of different types of attacks from people who want to steal your personal or company data. Connecting to these networks without considering the security implications will mean that any malicious individual lurking about could have complete and unrestricted access to the data you transmit and receive, including usernames and passwords as well as the data on your device. They could even install malware that could compromise your more secure devices at home or at work when you reconnect to those networks later.
One popular technique to exploit people looking for "free Wi-Fi" is to advertise a free hotspot which is in fact a malicious network to capture data or install malware on the devices that connect to it.
The best way to avoid the risks is to only connect to networks that you trust and if you really must connect to an unsecured Wi-Fi hotspot then use a VPN. A VPN will wrap traffic to and from your device in an encrypted tunnel to prevent it from being intercepted or captured.
If you'd like to know more about how you can protect yourself or your company, contact us today.
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week James is talking about public or insecure Wi-Fi.
Unsecured Public Wi-Fi is a minefield of security risks. If you're connecting to an unsecured access point or a network where the key is publicly available, such as an airport, coffee shop or public event then you're susceptible to a host of different types of attacks from people who want to steal your personal or company data.
Connecting to these networks without considering the security implications will mean that any malicious individual lurking about could have complete and unrestricted access to the data you transmit and receive, including usernames and passwords as well as the data on your device. They could even install malware that could compromise your more secure devices at home or at work when you reconnect to those networks later.
One popular technique to exploit people looking for "free Wi-Fi" is to advertise a free hotspot which is in fact a malicious network to capture data or install malware on the devices that connect to it. The best way to avoid the risks is to only connect to networks that you trust and if you really must connect to an unsecured Wi-Fi hotspot then use a VPN.
A VPN will wrap traffic to and from your device in an encrypted tunnel to prevent it from being intercepted or captured. If you'd like to know more about how you can protect yourself or your company, contact us today.
Cyber Weekly Flash Brief 21 August 2020: Uber infosec exec charged with cover-up, 50% anti-malware products fail, WFH security breach surge, 40% of firms sacked staff for cyber breaches during Covid
Cyber Weekly Flash Briefing 21 August 2020: Former Uber security exec charged with cover-up, half of anti-malware products fail to recognise threats, millions of social media accounts compromised by data breach, WFH causes surge in security breaches, staff 'oblivious' to best practices, 40% of firms have sacked staff for cyber security breaches during Covid, HMRC Investigating Over 10,000 COVID-Related Phishing Scams
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Former Uber security executive charged with data breach cover-up
Uber’s former chief security officer has been charged with obstruction of justice over accusations that he attempted to cover up a 2016 hack of the company, which exposed the personal details of 57m users and drivers.
Prosecutors said Joseph Sullivan, 52, hid the breach from the relevant authorities, and instead paid a ransom to the hackers and had them sign non-disclosure agreements stating, falsely, that they had not stolen personal information.
“The agreements contained a false representation that the hackers did not take or store any data,” prosecutors said in a press release. “When an Uber employee asked Sullivan about this false promise, Sullivan insisted that the language stay in the non-disclosure agreements.”
Mr Sullivan, who worked at Facebook prior to Uber, is said to have authorised the payment to the hackers of $100,000 in bitcoin, disguising the fee as coming via the company’s legitimate “bug bounty” programme — normally used to pay well-intentioned cyber security experts for discovering flaws and vulnerabilities.
It was not until November 2017, almost a year after Mr Sullivan allegedly knew the attack took place, that Uber revealed its knowledge of the breach and Mr Sullivan was dismissed.
Why this matters?
Not only was a criminal act conducted against Uber but a further criminal act was then conducted within the firm to cover it up. This shows what is at stake, that people will go to lengths to cover things up and that strong governance is needed and appropriate controls, and rewards, need to be in place across the organisation to encourage good behaviours.
Read more: https://www.ft.com/content/aff1fe76-418e-4f93-ba27-5a3c888c4252
Half of anti-malware products fail to recognize notable threats
Many of the most popular, well-established cyber security solutions do not protect their users from all notable threats, according to new analysis from SE Labs.
The security firm tested 14 of the world’s most popular cyber security solutions and, while products from Microsoft and Kaspersky Lab scored 100 percent, more than half failed to identify all threats.
"While the numbers of 'misses' are not out of this world, it's disappointing to see big brand products miss well-known threats," said Simon Edwards, CEO at SE Labs.
"Although we do 'create' threats by using publicly available free hacking tools, we don't write unique malware so there is no technical reason why any vendor being tested should do poorly."
According to SE Labs, the firm used common threats that affect the general public to conduct the tests, as well as more targeted forms of attack.
"In some cases the bad guys actually help us out, by sending our own organization the same types of malware that they use to target other potential victims. The Emotet malware campaign that ran in July of this year was a notable example," Edwards added.
With the Covid-19 pandemic forcing employees to remain at home, it has never been more important to protect devices and data from cyberthreats. Businesses and consumers alike are advised to keep their operating systems, applications and cybersecurity solutions up to date.
Why this matters:
Many firms put too much faith in technical controls, yet reports like this prove the point that technical controls are not as good as many people believe.Technical controls, even the best technical controls, only go so far when information security is a whole of business risk and people controls are needed in addition to technical controls to keep a firm safe.
Read more: https://www.itproportal.com/news/half-of-anti-malware-products-fail-to-recognize-notable-threats/
Hundreds of millions of Instagram, TikTok, YouTube accounts compromised by data breach
Security researchers have discovered an exposed database online which contains scraped data from the social media profiles of nearly 235m Instagram, TikTok and YouTube users.
For those unfamiliar with the practice, web scraping is an automated technique used to gather data from websites that is often employed by analytics firms who use it to create large databases of user information. Although the practice is legal, it is strictly prohibited by social media companies as it puts the privacy of their users and their data at risk.
Researchers discovered three identical copies of the exposed database online at the beginning of August. After examining the database they learned that it belonged to a company called Deep Social which has shut down its operations.
Why this matters
Big beaches like these, where data has been taken from different sources, breaches and public databases, can give attackers an incredible amount of data on you, probably enough to then start attacking your home or your employer. Even as far as identity theft type attacks.
Working from home causes surge in security breaches, staff 'oblivious' to best practices
The COVID-19 pandemic shows little sign of slowing down, and for many businesses, employees are still working remotely and from home offices.
While some companies are gearing towards reopening their standard office spaces in the coming months -- and have all the challenges associated with how to do so safely to face -- they may also be facing repercussions of the rapid shift to remote working models in the cyber security space.
In the clamor to ensure employees could do their jobs from home, the enterprise needed to make sure members of staff had the right equipment as well as network and resource access.
However, according to Malwarebytes, the rushed response to COVID-19 in the business arena has created massive gaps in cyber security -- and security incidents have increased as a result.
On Thursday, the cyber security firm released a report (.PDF), "Enduring from Home: COVID-19's Impact on Business Security," examining the impact of the novel coronavirus in the security world.
Company telemetry and a survey conducted with 200 IT and cyber security professionals suggest that since the start of the pandemic, remote workers have caused a security breach in 20% of organisations.
As a result, 24% of survey respondents added that their organizations had to pay unexpected costs to address cyber security breaches or malware infections after shelter-in-place orders were imposed.
Why this matters:
Months into this pandemic and staff working from home many staff are still oblivious to what they should and should not be doing and some firms are not doing a good enough job of getting their staff to appreciate the role they playing in helping to keep their firm’s safe.
Two-fifths of firms have sacked staff for cybersecurity breaches during Covid, poll shows
Almost two-fifths of business decision-makers (39 per cent) have dismissed employees because of a cyber security policy breach since the pandemic began, a survey has found.
The research polled 200 UK business decision-makers and found more than half (58 per cent) of firms believed that working from home made employees more likely to circumvent security protocols – including through the use of personal laptops and failing to change passwords.
To combat poor employee security practices, more than half (55 per cent) of those surveyed had banned, or planned to ban, staff from using personal devices to work from home.
Meanwhile, 57 per cent were implementing more measures to securely authenticate employees, including biometric data checks such as fingerprint and facial recognition technology, and multi-factor authentication steps to access certain files, applications and accounts.
The poll found that almost two-thirds (65 per cent) had made substantial changes to their cybersecurity policies in response to breaches and to Covid-19.
Why this matters:
It is imperative employers revisited their data security protocols in light of widespread home working. Employers need to communicate that the same principles of data protection apply at home as in the office, including that a breach could lead to severe disciplinary action. The importance of securing data and directing employees accordingly cannot be underestimated as the employer could find themselves responsible for significant data breaches if they have not taken appropriate steps to protect it.
Separately, a report by recruitment firm Robert Walters has found that up to 65,000 cyber attacks take place on UK SMEs every day, with 4,500 successful. The report, Cyber security: Building Business Resilience, found that almost half (48 per cent) of UK companies admitted to not having adequate cyber security provision to maintain a fully remote working model.
We are at the mercy of Google's cloud services – and it could cost us dearly
If the internet is our information superhighway, this week's mass outage of Google services represents the sudden and total closure of the M25.
Users up and down the country who rely on the system for their livelihoods found themselves confronted with the simple Gmail message: “Oops, something went wrong”. It was the digital equivalent of the Road Closed sign.
Such is the public and private sector’s dependence on software services provided by Google and its rivals Amazon, Microsoft and Alibaba that the five-hour outage will likely be felt at GDP level.
Never mind the frustration felt by hundreds of thousands of homeworkers, think of all the lost opportunities from meetings unattended, the lost confidence from work unsent and the lost productivity from reduced output.
It all adds up: a temporary internet shutdown costs an advanced economy like Britain’s £107m per day according to a report from Deloitte and Facebook into the economic impact of disruptions to connectivity.
That’s equivalent to 1.9 per cent of daily GDP. A big hit, especially in a recession when companies small and large are fighting for their lives and public services are stretched to the limit.
Why this matters
Firms are increasing reliant on a small number of providers and a loss of any one of those providers could have serious ramifications for any business operating online. It is always best to diversify your critical systems across different providers such that a loss of one does not have such wide reaching impact.
Four million Britons with Huawei phones risk their devices becoming obsolete
Up to four million British consumers could be stuck with increasingly useless and vulnerable Huawei mobiles after the Chinese firm was blocked from receiving future software updates due to US sanctions.
The crisis-hit company's phones are in danger of rapidly becoming obsolete following the expiry of a temporary licence allowing it to use apps and Android updates from Google - raising fears they could become increasingly slow and laden with bugs.
Huawei is at risk of being unable to renew the licence after being blacklisted by the Trump administration in May last year, with US companies barred from selling technology to it without explicit government approval.
As a result, Huawei phones using Google Mobile Services could stop getting new features and security updates from the US company.
The US claims that Huawei equipment can be used by the Chinese government for espionage – something which Huawei has repeatedly denied. Older Huawei phones, developed before May 2019, are still expected to have the support of critical security features.
Why this matters:
Security updates need to rolled out to keen devices and software secure once vulnerabilities have been found and fixed by vendors. If Huawei phones are no longer able to receive these security updates any vulnerabilities in the underlying operating system will be able to continue being exploited by cyber criminals or ironically nation state actors.
HMRC Investigating Over 10,000 COVID-Related Phishing Scams
More than 10,000 email, SMS, social media and phone scams exploiting the COVID-19 pandemic are being investigated by Her Majesty’s Revenue and Customs (HMRC) in the UK.
The official figures, published following a Freedom of Information (FOI) request highlight how the health and economic crisis has provided major scamming opportunities for cyber criminals.
The data showed that May was the month in which the highest number of phishing scams were reported by members of the public to HMRC, at 5152, representing a 337% rise compared to March when lockdown measures were first introduced in the UK. This was followed by 2558 reports in June, and 2105 in April. The total since March comes to 10,428.
Government programs introduced to support businesses and workers impacted by the lockdown have been a common target for scammers. Examples include an email purporting to be from HMRC regarding the government’s Coronavirus Job Retention Scheme, which attempted to get business owners to reveal their bank account information, while another offered a bogus tax rebate under the guise of the Self-Employment Income Support Scheme.
The FOI also showed that 106 COVID-related websites have been requested for removal since March, with April the highest month at 42, followed by 24 in May and 17 in March. In May, it was revealed that HMRC formally asked internet service providers (ISPs) to remove 292 scam web addresses exploiting the coronavirus outbreak.
Why this matters:
Cyber criminals will always take advantage of current events, crises and tragedies to exploit unsuspecting victims. This has never been so evident as with the current Coronavirus pandemic, especially with the shift to more staff working from home.
Read more: https://www.infosecurity-magazine.com/news/hmrc-investigating-covid-related/
Can you have too much security? Cyber Tip Tuesday for 18 August 2020
Surely more security is always better right? Surely you can’t have too much? Maybe not - find out more
Cyber Weekly Flash Briefing 14 August 2020: Travelex goes bust following ransomware, Microsoft fix 120 vulns inc two zero-days, more ransomware victims paying up, Cloud misconfigurations create risks
Cyber Weekly Flash Briefing 14 August 2020: Travelex Forced into Administration After Ransomware Attack, Microsoft fixes 120 vulnerabilities inc two zero-days, More ransomware victims are paying up, Misconfiguration #1 Cloud Security Threat, Beware What You Ask Amazon Alexa, Ex-Uber engineer sentenced to 18 months in prison for stealing driverless car secrets from Google, Google and Amazon are now the most imitated brands for phishing
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Travelex Forced into Administration After Ransomware Attack
Ransomware victim Travelex has been forced into administration, with the loss of over 1000 jobs.
PwC announced late last week that it had been appointed joint administrators of the currency exchange business.
The Sodinokibi (REvil) ransomware variant is believed to have struck the firm on New Year’s Eve last year, forcing its website offline and impacting its bricks-and-mortar stores and banking services. It took until January 17 for the firm to get its first customer-facing systems live again in the UK.
Why this matters:
Firms of any size can call victim to ransomware and many firms will not survive a significant cyber event such as this. Unconfirmed reports at the time suggested that a critical unpatched vulnerability in a VPN (Virtual Private Network) may have allowed attackers to remotely execute malicious code. A security researcher said he reached out to the firm in September 2019 to flag the issue but was ignored. This again shows the importance of ensuring all security updates are applied quickly. Has this software had the security updates applied those vulnerabilities would not have been able to be used in this attack.
Read more: https://www.infosecurity-magazine.com/news/travelex-forced-administration/
Microsoft August 2020 Patch Tuesday fixes 120 vulnerabilities, two zero-days
Microsoft’s August 2020 Patch Tuesday security updates fell this week and this month the company has patched 120 vulnerabilities across 13 different products, from Edge to Windows, and from SQL Server to the .NET Framework.
Among these 120 vulnerabilities, 17 bugs have received the highest severity rating of "Critical," and there are also two zero-days — vulnerabilities that have been exploited by hackers before Microsoft was able to provide a fix.
Why this matters:
All security updates should be applied as soon as possible to prevent vulnerabilities from being exploited in attacks. When vulnerabilities are announced criminals will waste no time in weaponizing them (creating exploits to use in attacks) so the quicker the vulnerabilities are closed the safer you will be.
More ransomware victims are paying up, even when data recovery is possible
The proportion of ransomware attack victims actually paying ransoms increased in the last quarter, even in instances where ransomed data could be recovered, new figures have revealed.
According to a commercial ransomware recovery service, data exfiltration attacks are becoming more common and blending with traditional ransomware hacks. Data exfiltration extortion involves an attacker taking possession of stolen data and putting it up for sale on forums or marketplaces. Once monetised, the hacker asks the victim to pay a ransom to prevent the information’s release.
The recover firm added that tools currently on the market vary wildly when it comes to data recovery success following a ransomware attack. What’s more, the company has noted an uptick in the number of companies experiencing operating system and registry corruption even after ransomed data is restored.
Why this matters:
It used to be that backups were the best defence against ransomware attacks, but if your data is stolen a backup won’t help you avoid having to pay out to keep your sensitive or confidential data out of the public domain.
Intel, SAP, and Citrix release critical security updates
Intel released 18 advisories, including fixes for Denial of Service, Information Disclosure and Elevation of Privilege flaws affecting various products on Windows, Chrome OS and Linux OS.
SAP’s released 15 security notes and an update to a previously released one to address flaws in a variety of offerings, including SAP ERP, SAP Business Objects Business Intelligence Platform, SAP S/4 HANA and various SAP NetWeaver components.
Citrix’s has released patches for a set of vulnerabilities in certain on-premises instances of Citrix Endpoint Management (aka XenMobile Server).
Why this matters:
Security upgrades should always be applied as soon as possible. Whether announced vulnerabilities are already being exploited or not as they become known they likely will be exploited and patching them (applied the fixes made available) prevent them from being exploited.
Read more: https://www.helpnetsecurity.com/2020/08/12/intel-sap-citrix-security-updates-august-2020/
IT Pros Name Misconfiguration #1 Cloud Security Threat
Configuration errors are the number one threat to cloud security, according to a new poll of IT and security professionals.
A security vendor interviewed 653 industry professionals to compile its 2020 Cloud Security Report.
Three-quarters (75%) claimed to be “very” or “extremely” concerned about cloud security, with most (52%) believing that the risks are higher in the public cloud than on-premises.
The top four threats were cited as: misconfiguration (68%), unauthorized cloud access (58%), insecure interfaces (52%), and account hijacking (50%).
These security concerns have created multiple barriers to further adoption of cloud services. The top inhibitor of adoption was a lack of qualified staff (55%), up from fifth place last year.
This may go some way to explaining respondents’ concerns around configuration errors, especially as 68% of these organisations are using two or more public cloud providers — adding to the complexity.
Why this matters?
Organisations’ cloud migrations and deployments are racing ahead of their security teams’ abilities to defend them against attacks and breaches. Their existing security solutions only provide limited protections against cloud threats, and teams often lack the expertise needed to improve security and compliance processes
Read more: https://www.infosecurity-magazine.com/news/misconfiguration-error-cloud/
RedCurl cybercrime group has hacked companies for three years
Security researchers have uncovered a new Russian-speaking hacking group that they claim has been focusing on the past three years on corporate espionage, targeting companies across the world to steal documents that contain commercial secrets and employee personal data.
Named RedCurl, the activities of this new group have been detailed in a 57-page report released this week.
Researchers have been tracking the group since the summer of 2019 and have since identified 26 other RedCurl attacks, carried out against 14 organisations, going as far back as 2018.
Why this matters:
This Russian group have targeted victims across different countries and industry sectors, and included construction companies, retailers, travel agencies, insurance companies, banks, and law and consulting firms from countries like Russia, Ukraine, Canada, Germany, Norway, and the UK. Many firms could fall victim to cyber crime groups like this if their defences are not able to withstand such attackers.
Read more: https://www.zdnet.com/article/redcurl-cybercrime-group-has-hacked-companies-for-three-years/
Why You Must Beware What You Ask Amazon Alexa
The same cyber team that cracked open TikTok, WhatsApp, Microsoft’s cloud and even Philips lightbulbs has just turned its attention to Amazon’s Alexa. And, unsurprisingly, it hasn’t disappointed. After “speculating” that Amazon’s 200 million devices “could be a prime entry-point for hackers,” Check Point Research has just lifted the lid to unmask “serious security flaws in Alexa.” According to the team, “in just one click, a user could have given up their voice history, home address and control of their Amazon account.”
Why this matters:
Warnings about the dangers of smart speakers and their extended families of virtual assistants are not new. These are the same devices that causes such scandal last year, when it transpired humans were listening to conversations to better train the AI. The issue here is different, much more akin to the broader problem of IoT security. Every different gadget you connect to the internet becomes a potential vulnerability and the methods needed to crack Amazon’s devices were not particularly sophisticated.
Ex-Uber engineer sentenced to 18 months in prison for stealing driverless car secrets from Google
A star engineer who admitted stealing self-driving car secrets from Google has been sentenced to 18 months in prison.
Anthony Levandowski, who helped found Google's self-driving car project, now known as Waymo, pleaded guilty to downloading documents containing data about the company's work and accessing one of them after he had left to found his own trucking startup.
Sentencing him in a San Francisco court, the judge said he was imposing prison time as a deterrent.
An early star in the self-driving car scene, Mr Levandowski pushed for Google to develop the technology but later became disillusioned, leaving in early 2016 to start trucking company Otto, which was bought by Uber less than eight months later.
Waymo sued Uber, a case which was settled in 2018, with Uber paying out $245m (£187m) in equity and agreeing not to use its technology.
Uber had signed an indemnification agreement with Mr Levandowski, forcing it to pay his legal fees, but has refused to pay a $179m debt he owes to the Google spin-out, a consequence of separate legal action relating to his departure.
Why this matters:
Your staff present one of your biggest risks, and a disgruntled or disillusioned employee can be very dangerous. The theft of intellectual property for personal gain is a classic example of this kind of behaviour. Data Loss Prevention (DLP) systems can help to spot unusual behaviour in employees and detect sensitive data being extracted from corporate systems.
Google and Amazon are now the most imitated brands for phishing
You may want to think twice about opening that email claiming to be from Google or Amazon, after new research found the tech giants were being used as lures for phishing scams.
Earlier this year, Check Point revealed that Apple was the most imitated brand for phishing, but over the course of the last few months, the iPhone maker has fallen to seventh place with Google and Amazon now taking the top spots.
Why this matters:
Phishing is estimated to be the starting point of over 90 percent of all cyberattacks and according to Verizon's 2019 Data Breach Investigations Report, nearly one third (32%) of all data breaches involved phishing activity. Additionally phishing was present in 78 percent of cyber espionage incidents and the installation and use of backdoors in company networks.
Read more: https://www.techradar.com/news/google-and-amazon-are-now-the-most-imitated-brands-for-phishing
Regulatory Expectations around Cyber and Information Security - Cyber Tip Tuesday video for 11 August 2020
Welcome to this week's Black Arrow Cyber Tip Tuesday. We have talked before about how the regulators like the Guernsey GFSC and the Jersey JFSC expect Boards to take Cyber and information security seriously by the Board just as they do with more established risks, and that Directors are required to understand and manage those risks. So, how can a Board evidence this. The clearest way is to schedule a regular review of a cyber security report at Board meetings. That report should contain a few sections with brief and focused content that is explained in terminology that all business leaders can understand. One of those sections is a dashboard with key indicators about the risks that the business faces, and the controls that are in place to mitigate those risks to match the organisation’s risk appetite. We recommend that organisations structure their risks and controls based on one of the globally recognised frameworks, for example NIST or ISO 27001. In fact, the forthcoming regulations from the GFSC are based on the NIST framework. So, the dashboard would also be structured to match that same framework, to ensure everything this covered. The Board members should be sufficiently knowledgeable about these topics to be able to question whether things are as good as the dashboard says they are, and whether the rating should be Amber instead of Green. Or, whether the RAG threshold is appropriate for their business. And that challenge in the Board room should be minuted for future reference. You don’t need to be an expert, but you do need to have a good understanding of the basics, and your independent trusted advisors can support you on the details. Contact us to see how we can help you achieve what the regulators require of you.
Welcome to this week's Black Arrow Cyber Tip Tuesday.
We have talked before about how the regulators like the Guernsey GFSC and the Jersey JFSC expect Boards to take Cyber and information security seriously by the Board just as they do with more established risks, and that Directors are required to understand and manage those risks.
So, how can a Board evidence this.
The clearest way is to schedule a regular review of a cyber security report at Board meetings. That report should contain a few sections with brief and focused content that is explained in terminology that all business leaders can understand. One of those sections is a dashboard with key indicators about the risks that the business faces, and the controls that are in place to mitigate those risks to match the organisation’s risk appetite.
We recommend that organisations structure their risks and controls based on one of the globally recognised frameworks, for example NIST or ISO 27001. In fact, the forthcoming regulations from the GFSC are based on the NIST framework. So, the dashboard would also be structured to match that same framework, to ensure everything this covered.
The Board members should be sufficiently knowledgeable about these topics to be able to question whether things are as good as the dashboard says they are, and whether the rating should be Amber instead of Green. Or, whether the RAG threshold is appropriate for their business. And that challenge in the Board room should be minuted for future reference.
You don’t need to be an expert, but you do need to have a good understanding of the basics, and your independent trusted advisors can support you on the details.
Contact us to see how we can help you achieve what the regulators require of you.
Cyber Weekly Flash Briefing 07 August 2020: INTERPOL warn on alarming pace of cyber crime, Canon ransomware, Garmin paid ransom, TV Licence fraud targets elderly, Netgear won’t patch vuln routers
Cyber Weekly Flash Briefing 07 August 2020: INTERPOL warning on “Alarming Pace” of cyber crime, Capital One fined $80m, Canon ransomware attack, Garmin reportedly paid multimillion ransom, Over-75s warned of rise in TV Licence 'phishing' fraud, Netgear Won’t Patch 45 Router Models Vulnerable to Serious Flaw
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
INTERPOL: Cyber crime Growing at an “Alarming Pace” Due to #COVID19
Cyber crime is growing at an “alarming pace” as a result of the ongoing COVID-19 crisis and is expected to accelerate even further, a new report from INTERPOL has found.
It revealed the extent to which cyber-criminals are taking advantage of the increasing reliance on digital technology over recent months. This includes the rapid shift to home working undertaken by many organisations, which has involved the deployment of remote systems and networks, often insecurely.
Based on feedback from member countries, INTERPOL said that during the COVID-19 period, there has been a particularly large increase in malicious domains (22%), malware/ransomware (36%), phishing scams/fraud (59%) and fake news (14%).
Threat actors have revised their usual online scams and phishing schemes so that they are COVID-themed, playing on people’s economic and health fears.
Why this matters:
Increases in malicious activity is always a concern, especially when firms don’t realise how bad the situation is already and fail to grasp how much worse it is getting. Cyber criminals have gone through an industrial revolution and have built criminal organisations to rival some of the biggest legitimate business empires. Increases in threats require and increase in defensive capability, across IT, people and governance, to counter this rising tide.
Read more: https://www.infosecurity-magazine.com/news/cybercrime-growing-alarming-pace/
Capital One fined $80m for data breach
Capital One, one of the top five credit card issuers by balances in the US, has been fined $80m and ordered to improve internal controls after regulators identified a string of failings that allowed hackers to obtain the personal data of more than 106m customers and credit card applicants last year.
The bank was found to have failed to establish effective risk assessment processes prior to migrating significant information technology operations to the public cloud, as well as failing to quickly correct deficiencies.
The data breach exposed names, addresses, phone numbers, self-reported income, credit scores and payment history, as well as some people’s social security numbers.
It has become a cautionary tale for banks migrating their data from their own physical IT to the kind of virtual clouds that the Capital One data was hacked from.
Why this matters:
Moving to the cloud can open up new risks and misconfigurations can go undetected until they are exploited by malicious actors. It is important to make sure you know where the weaknesses and vulnerabilities are before someone else does, and this included cloud infrastructure.
Read more: https://www.ft.com/content/a730c6a0-c362-4664-a1ae-5faf84912f20
Canon confirms ransomware attack in internal memo
Canon appears to be latest in a number of large high profile firms in recent weeks to suffer a ransomware attack that has had an impact on numerous services, including Canon's email, Microsoft Teams, USA website, and other internal applications. In an internal alert sent to employees, Canon has disclosed the ransomware attack and working to address the issue.
Researchers were alerted by a suspicious outage on Canon's image.canon cloud photo and video storage service resulting in the loss of data for users of their free 10GB storage feature.
However, the final status update was strange as it mentions that while data was lost, "there was no leak of image data." This led BleepingComputer to believe there was more to the story and that they suffered a cyberattack.
Why this matters:
Any firm of any size can fall victim to ransomware and recovering can be time consuming, expensive and cause significant reputational damage. These attacks invariably stem from users clicking on links in phishing emails, something that IT departments and technical controls aren’t capable of defending against on their own.
Read more: https://www.bleepingcomputer.com/news/security/canon-confirms-ransomware-attack-in-internal-memo/
Garmin reportedly paid multimillion-dollar ransom after suffering cyberattack
Following on from Canon being the latest high profile victim, reports indicate that fitness wearable and satellite navigation brand Garmin paid millions of dollars in ransom after an attack took many of its products and services offline last month. The payment was reportedly made through a ransomware negotiation company in order for Garmin to recover data held hostage as a result of the attack.
It was reported last week that Garmin had received a decryption key to access data encrypted by the virus, and that the initial ransom demand was for $10 million.
Why this matters:
If a company had to resort to paying the ransom then it can be inferred that they were unable to recover their data, had insufficient backups or had never tested recovering from backups and when they needed to for real found they were unable. It’s too late to find out when you need something that you don’t have it.
If no firm or individual paid ransoms this problem would go away. For as long as even a small number of firms and individuals pay this will continue to be a massive problem, affecting everyone.
Read more: https://www.theverge.com/2020/8/4/21353842/garmin-ransomware-attack-wearables-wastedlocker-evil-corp
Google: Eleven zero-days detected in the wild in the first half of 2020
According to data collected by Google's Project Zero security team, there have been 11 zero-day vulnerabilities exploited in the wild in the first half of the year.
The current number puts 2020 on track to have just as many zero-days as 2019 when Google security researchers said they tracked 20 zero-days all of last year.
Details about these zero-days have been obtained from a spreadsheet managed by Google security researchers, which the company made public available earlier this year. The spreadsheet contains Google's internal statistics about in-the-wild zero-day usage going as far back as 2014, when the company began tracking said stats.
Why this matters:
Zero-days are vulnerabilities for which fixes have not yet been made available and as such as difficult to defend against. Good security is all about having multiple layers of controls and if you have good procedural, people and governance controls in place this should still go a good way to helping to defend against zero-days.
As soon as security updates are made available they should ideally be tested and applied on all applicable devices as soon as possible to prevent vulnerabilities from being exploited.
TeamViewer flaw could be exploited to crack users’ password
A high-risk vulnerability (CVE-2020-13699) in TeamViewer for Windows could be exploited by remote attackers to crack users’ password and, consequently, lead to further system exploitation.
TeamViewer is an application that is used primarily for remote access to and control of various types of computer systems and mobile devices, but also offers collaboration and presentation features (e.g., desktop sharing, web conferencing, file transfer, etc.)
Since the advent of COVID-19, enterprise use of the software has increased due to many employees being forced to work from home.
Why this matters:
Credentials stolen from any successful breach are likely to be used in credential stuffing attacks (where the same usernames and passwords are reused) against other sites and services.
Read more: https://www.helpnetsecurity.com/2020/08/06/cve-2020-13699/
Qualcomm chip vulnerability puts millions of phones at risk
Smartphone devices from the likes of Google, LG, OnePlus, Samsung and Xiaomi are in danger of compromise by cyber criminals after 400 vulnerable code sections were uncovered on Qualcomm’s Snapdragon digital signal processor (DSP) chip, which runs on over 40% of the global Android estate.
To exploit the vulnerabilities, a malicious actor would merely need to convince their target to install a simple, benign application with no permissions at all.
Why this matters:
The vulnerabilities leave affected smartphones at risk of being taken over and used to spy on and track their users, having malware and other malicious code installed and hidden, or even being bricked outright. Hopefully a fix will be forthcoming but it looks like it might be months before this fix is widely available.
Read more here: https://www.computerweekly.com/news/252487274/Qualcomm-chip-vulnerability-puts-millions-of-phones-at-risk
Over-75s warned of rise in TV Licence 'phishing' fraud
Over-75s awaiting letters about their new licence fee payments are falling victim to fraudsters, it has emerged.
The BBC has told 4.5 million pensioners to expect a letter from TV Licensing advising them on how to set up payment, as the free scheme for over-75s ended on July 31.
But the corporation has not given an indication of when the communication will arrive or what the wording will be, and in the meantime pensioners are being duped by scam emails which purport to be official.
The National Cyber Security Centre, part of GCHQ, said the number of licence fee “phishing” emails had risen in July, compared to previous months, and it was working hard to block them.
A spokesman said: “It is despicable that criminals are targeting over-75s in this way. TV Licensing would never ask for payment details over an email, so as soon as we were alerted to the scam messages sent in this callous campaign, they were immediately blocked.
Why this matters:
Cyber criminals are unscrupulous and will happily target the most vulnerable members of our society. If you have elderly relatives make them aware of these scams and encourage them not to respond for requests sent via email.
Read more: https://www.telegraph.co.uk/news/2020/08/03/over-75s-warned-rise-tv-licence-phishing-fraud/
Netgear Won’t Patch 45 Router Models Vulnerable to Serious Flaw
Netgear will not patch 45 router models that are vulnerable to a high-severity remote code execution flaw, the router company revealed last week. However, the company says that routers that won’t receive updates are outdated or have reached EOL (End of Life).
The remote code execution vulnerability in question, which was disclosed June 15, allows network-adjacent attackers to bypass authentication on vulnerable Netgear routers – sans authentication. The high-severity flaw affects 79 Netgear Wi-Fi routers and home gateway models – but Netgear says that 45 of those router models are outside of its “security support period.”
Why this matters:
If you are using a Netgear device ensure that it is not in the list of devices that are no longer supported and if necessary replace it with a different router that is supported. If the device you own is still supported you should log into the web interface and ensure that it is updated to the most recent version of firmware to include any security updates.
Many people never update the firmware on their networking devices at home and this means that there can be a significant number of significant security vulnerabilities that have gone unfixed jeopardising the security of any devices connected to that router. If you don’t know how to update home networking devices contact someone who can help you to do this.
Read more: https://threatpost.com/netgear-wont-patch-45-router-models-vulnerable-to-serious-flaw/157977/
Free Advisory Sessions for Startups and Entrepreneurs - Cyber Tip Tuesday video 04 August 2020
Free Advisory Sessions for Startups and Entrepreneurs - Cyber Tip Tuesday video 04 August 2020
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week Tony talks about free advisory sessions for startups and entrepreneurs to help them think about security as they take their first steps with their new businesses.
When setting up a new business there are lots and lots of things to think about, and probably many things will come up that you never knew to think about, but security is not something that should be bolted on afterwards but rather something that should be thought about from the start.
Thinking about security from the start will always put you in a better position after all no business can afford a data breach or significant cyber event and most new businesses and startups won’t survive if they are attacked. A mistake small businesses make is thinking they don’t need to worry about cyber security but nearly half of all attacks hit small businesses so this is not something only larger firms need to think about.
The controls that startups and small business should put in place are often fairly basic and most come with no or little cost attached so are within the reach of all firms no matter how small – and these controls help to protect against the vast majority of attacks. If you’re a new startup or entrepreneur contact us today to arrange a free chat to you on the right track to defending your new business.